Information Security
Basic Concept
The Olympus Group considers information security risks to be important risks that not only directly affect our business but could also have a serious impact on our customer medical institutions, and even on medical care itself. Also, appropriate information security risk management and incident response are becoming increasingly important in terms of maintaining and enhancing the Company's sustainable growth and the competitive advantage of our products and services. With regard to addressing information security risks, we believe it is important that the measures are being driven on a whole companywide basis, not limiting them to information security dedicated departments. Not only the importance of internal collaboration, it is also crucial to actively communicate and collaborate with our customer medical institutions, business partners, industry associations, and government agencies.
Under the corporate strategy announced in 2019, we are implementing our corporate transformation plan "Transform Olympus" with the aim of transforming ourselves into a corporate culture and corporate structure capable of sustainable growth. As part of this plan, we are promoting the globalization of each function, standardization of processes, and centralization of risk management. In the area of information security and privacy compliance, we have established a new strategy in the fiscal year ended March 31, 2022, in order to visualize risks from the perspective of corporate risk management with uniform standards across the global group and to ensure that risk mitigation activities in each related function are comprehensive and harmonized. This strategy includes the creation of a new governance model and a multi-year strategic roadmap corresponding to the companywide transformation. Through the implementation of our new governance model and strategy, we are particularly focused on achieving the following:
- Increase resilience to cyber-attacks not only in our general IT systems, but also in our products and services, their development and manufacturing environments.
- Continuously ensure product security throughout the entire product lifecycle, including the supply chain, to ensure a consistent supply of products and services.
- Protect, manage, and securely utilize data of various types and confidentiality levels while further enhancing privacy protection based on the latest trends and regulations in each country and region.
Information Security Governance
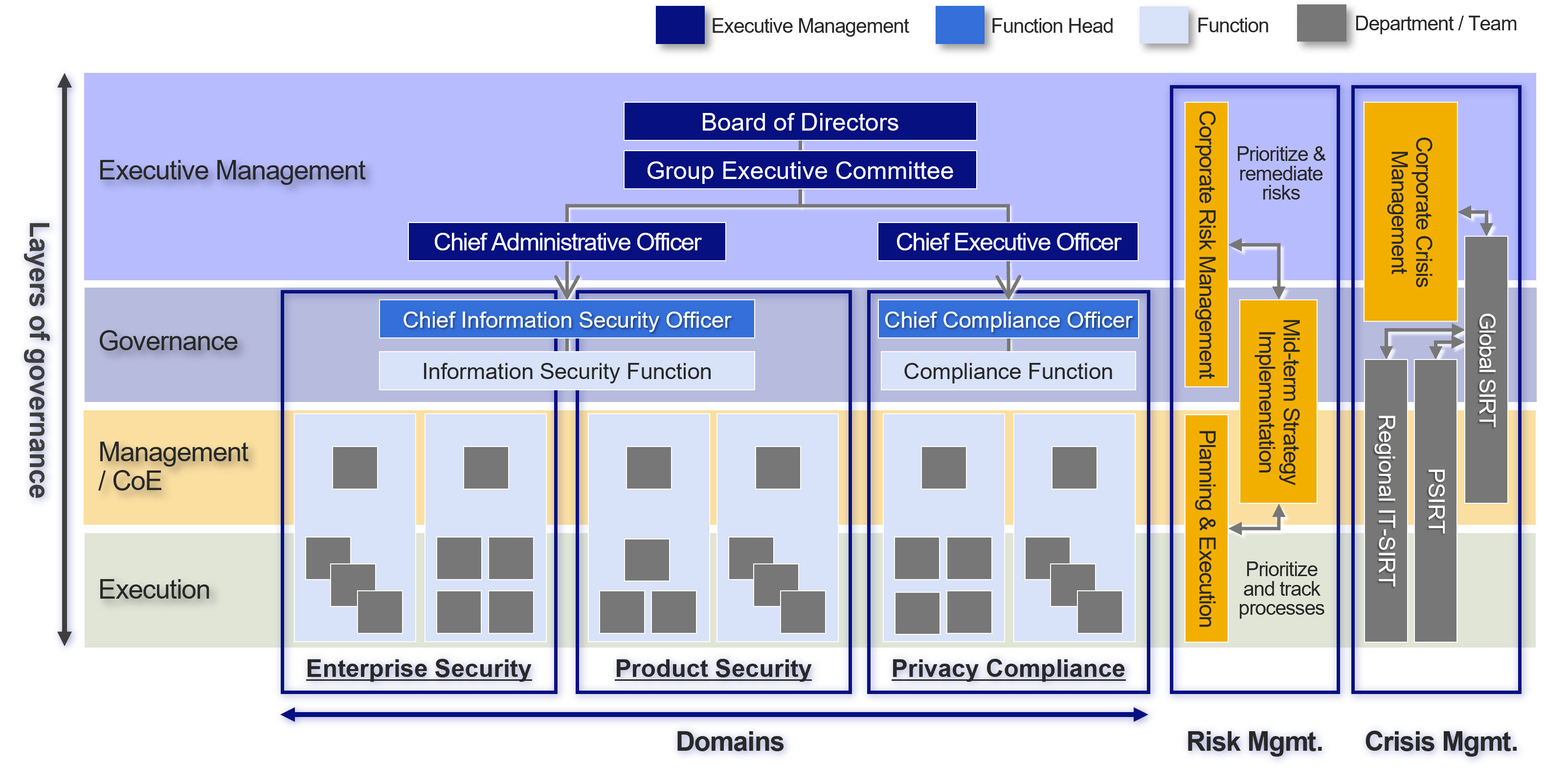
For the effectiveness of security measures, companywide approach is crucial and thus clear management involvement and leadership is necessary. For this purpose, our Chief Administrative Officer (CAO)*1 owes accountability for information security, and the Chief Information Security Officer (CISO) and a dedicated organization directly under the CAO are responsible for the group-wide risk management of information security and the formulation and implementation of strategies based on that risk management. The CAO and the CISO report to the Board of Directors on the status of information security for the entire Olympus Group on a regular basis*2 and as needed in response to changes in the environment, and the Board of Directors supervises overall execution regarding information security.
In terms of the execution structure, depending on varied requirements in security capability and capacity by function, the following three-layer model is being applied to the security organizational development with a view of both effectiveness and efficiency: the Governance Layer, which oversees the formulation and execution of Group-wide information security strategies; the Management/CoE Layer, which oversees the formulation and execution of plans within each function and department based on the formulated strategies; and the Execution Layer, which is responsible for execution within each function and department.
We have clarified the responsibilities and collaboration methods for information security based on the following two domains. Enterprise Security - information security including general IT systems and data governance and Product Security - information security of our products and services. As for promoting understanding of and ensuring compliance with important laws, regulations, and internal rules related to the protection of personal information (Privacy Compliance,) we are promoting the enhancement of the structure under the supervision of the Chief Compliance Officer (CCO). (For more information on Compliance, please refer to this page.)
For risk management, the CISO and the dedicated organization conduct a Group-wide risk assessment, considering various external factors such as trends of cyber-attacks outside the Company and best practices in the industry, etc. Based on the risk assessment, the CISO and the dedicated organization formulate a medium-term strategy, taking into account our business strategy, customer requirements, and legal and regulatory trends. Each function and department then implement risk mitigation measures based on the established strategy, thereby ensuring that risk mitigation is based on uniform standards and balanced throughout the Group.
In the event of a cyber-attack, it is important to have a crisis management system that can respond promptly, coordinate with the entire Group and related organizations, and management decisions on group-wide basis are appropriately made. Therefore, in addition to IT-SIRT in each region and PSIRT that are responsible for rapid incident containment and recovery, we are working to build a Global SIRT structure that supports collaboration among the regions and functions/departments, coordination with related organizations, and decision-making by the executive management team.
Number of Information Security Incidents and Breaches*3
The table below shows the number of incidents and breaches globally over the past three years. In the fiscal year ended March 31, 2022, IT systems in some regions in EMEA (Europe, the Middle East, and Africa) and the Americas (the United States, Canada, and Latin America) were subject to unauthorized access. Incident response was implemented in the affected areas, and various security enhancements were made based on the results of the analysis of those incidents. While no evidence of loss, misuse, or leakage of the Company's data was confirmed as a result of the unauthorized access in the EMEA region, some data may have been compromised in the Americas region. We have notified those who may have been affected.
| Item | FY2020 | FY2021 | FY2022 |
|---|---|---|---|
| Number of information security breaches or other cybersecurity incidents | 0 | 0 | 4 |
| Number of information security breaches related to leaks of customers' personal information | 0 | 0 | 4 |
| Number of customers affected by the company's data breach | 0 | 0 | - |
| Amount of penalties / fees paid in connection with information security breaches or other cybersecurity incidents | 0 | 0 | 0 |
Related Corporate News
- Investigating potential cybersecurity incident affecting limited areas of our EMEA IT system (September 11, 2021)
- Update: Olympus Investigation Into Cybersecurity Incident Ongoing (September 14, 2021)
- Investigating potential cybersecurity incident affecting our IT system in the Americas (October 12, 2021)
- Update: Investigation into cybersecurity incident ongoing (October 19, 2021)
- Update about cybersecurity incident in the U.S. – systems restored (November 16, 2021)
Related Information
- Olympus Group Information Security Policy
- The Olympus Group Personal Information Protection Policy (Translation)
- Management Policies: Business Risks
- (Reference) Participation in a simulation drill for a cyber attack (Medical Cyber Security Council, May 19, 2021) - Japanese only

*1 The current CAO has a diverse background that includes experience in the information security and cybersecurity field, such as overseeing project management of IT system installations and supervising IT security risk assessments.
*2 Regular reports are made to the Group Executive Committee on a quarterly basis and to the Board of Directors on an annual basis.
*3 The figures in the table are based on the disclosure standards of GRI 418-1 (2016). In case it is difficult to disclose a definite figure due to ongoing investigation or monitoring of the possible impact of an incident, the figure is shown as "-".

